NPM, the backbone of the modern JavaScript ecosystem, has suffered its most significant supply chain compromise to date. The scale is enormous, with more than 2.6 billion weekly downloads affected.
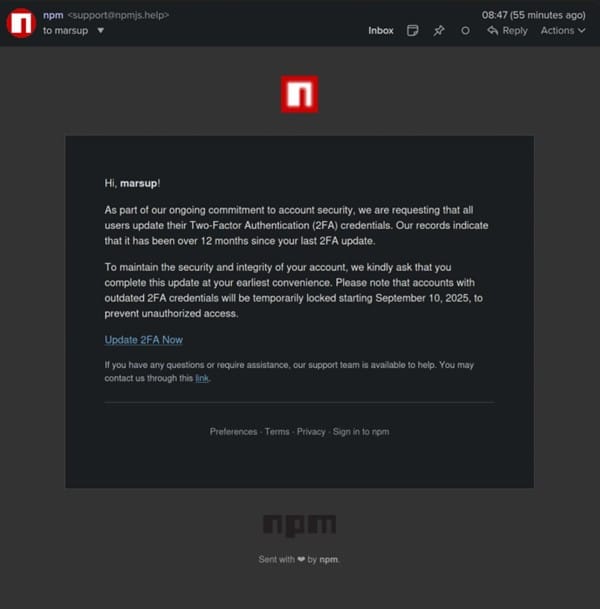
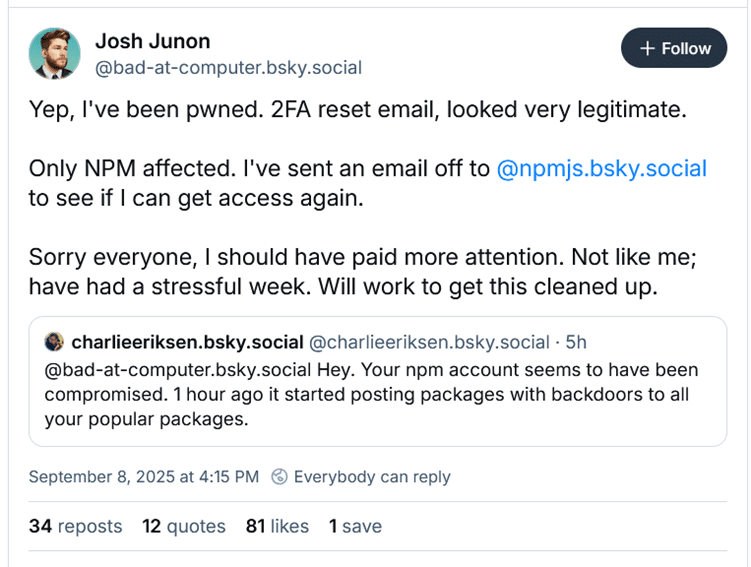
The breach began with the compromise of package maintainer Josh Junon’s accounts. Attackers bypassed protections by exploiting a 2FA reset email. Once inside, they published malicious updates to widely used NPM libraries. Junon confirmed the compromise publicly, sharing both the phishing email and screenshots of the takeover.
The attack was multi-layered. In addition to injecting malicious code into packages, the attackers also set up a credential-harvesting site. The domain they used for phishing also hosted a clone of the official npm[.]js site, designed to capture developer credentials directly.
The scope of impacted packages is unprecedented. Some of the most widely downloaded NPM modules were compromised, including:
• chalk (299.99m weekly downloads)
• debug (357.6m)
• ansi-styles (371.41m)
• supports-color (287.1m)
• strip-ansi (261.17m)
• color-convert (193.5m)
• ansi-regex (243.64m)
• color-name (191.71m)
• is-arrayish (73.8m)
• slice-ansi (59.8m)
• error-ex (47.17m)
• color-string (27.48m)
• simple-swizzle (26.26m)
• chalk-template (3.9m)
• backslash (0.26m)
These libraries sit at the base of countless dependency chains. The infection, therefore, cascades across millions of projects, even if developers never imported the compromised packages directly.
The fallout is immediate. Continuous integration pipelines around the world are now failing npm audits. Organizations are scrambling to identify if their builds pulled in the malicious versions. Given the ubiquity of packages like chalk and debug, it is likely that the compromise has reached into production environments at scale.
This incident highlights a persistent fragility in the open-source supply chain. Centralized ecosystems like NPM magnify both the benefits of reusable code and the risks of compromise. Developers have little visibility into transitive dependencies and often little recourse when upstream maintainers are targeted.
For now, security teams should audit their dependency trees, pin safe versions, and monitor NPM advisories closely. The situation is evolving, and further disclosures are likely as investigators untangle the breadth of the attack.
Further reading and ongoing coverage:
• https://news.ycombinator.com/item?id=45169794
• https://github.com/github/advisory-database/issues/6099




